Old-05 Domain & Tool
- 구분 : 쿠키 조작, 파라미터 조작
- 문제풀이에 사용된 도구
- Chrome 103.0.5060.66 관리도구[F12]
- Burp Suite Community Edition v2022.6.1
Old-05 Question & Answer
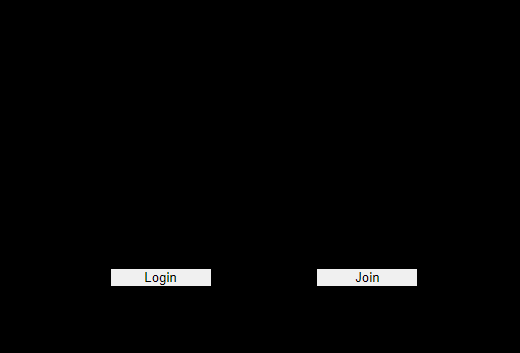
들어가면 아무것도 없는 버튼2개의 php화면이 우리를 반겨준다. 버튼을 각각 누르면 다음과 같이 동작한다.


왼쪽사진은 login.php를 , 오른쪽 사진은 join.php를 실행하였을때의 사진이다. 일단 Join을 들어가서 login동작을 확인하고 싶다. 들어갈 수 있는 login.php에서 힌트를 조금 얻어보자

- login.php는 mem이라는 폴더아래 있다. 만약 여기서 Directory Traversal이 가능하다면?? mem의 폴더가 어떤 약어로 쓴지는 모르겠지만, 아래에 있는 모든 폴더가 확인가능할 거이다. login.php를 지우고 mem/으로 끝나게 url을 바꾸어보자

와우. 들어왔다. 이곳에서 join.php를 클릭해보자 Access_denied라고 뜨기는 하면서 화면이 안나온다. 다만 검은화면에서 멈추어 있는데, 소스코드를 확인해보자 다음과 같은 html소스코드를 확인할 수 있다.
<html>
<title>Challenge 5</title></head><body bgcolor=black><center>
<script>
l='a';ll='b';lll='c';llll='d';lllll='e';llllll='f';lllllll='g';llllllll='h';lllllllll='i';llllllllll='j';lllllllllll='k';llllllllllll='l';lllllllllllll='m';llllllllllllll='n';lllllllllllllll='o';llllllllllllllll='p';lllllllllllllllll='q';llllllllllllllllll='r';lllllllllllllllllll='s';llllllllllllllllllll='t';lllllllllllllllllllll='u';llllllllllllllllllllll='v';lllllllllllllllllllllll='w';llllllllllllllllllllllll='x';lllllllllllllllllllllllll='y';llllllllllllllllllllllllll='z';I='1';II='2';III='3';IIII='4';IIIII='5';IIIIII='6';IIIIIII='7';IIIIIIII='8';IIIIIIIII='9';IIIIIIIIII='0';li='.';ii='<';iii='>';lIllIllIllIllIllIllIllIllIllIl=lllllllllllllll+llllllllllll+llll+llllllllllllllllllllllllll+lllllllllllllll+lllllllllllll+ll+lllllllll+lllll;
lIIIIIIIIIIIIIIIIIIl=llll+lllllllllllllll+lll+lllllllllllllllllllll+lllllllllllll+lllll+llllllllllllll+llllllllllllllllllll+li+lll+lllllllllllllll+lllllllllllllll+lllllllllll+lllllllll+lllll;if(eval(lIIIIIIIIIIIIIIIIIIl).indexOf(lIllIllIllIllIllIllIllIllIllIl)==-1) {alert('bye');throw "stop";}if(eval(llll+lllllllllllllll+lll+lllllllllllllllllllll+lllllllllllll+lllll+llllllllllllll+llllllllllllllllllll+li+'U'+'R'+'L').indexOf(lllllllllllll+lllllllllllllll+llll+lllll+'='+I)==-1){alert('access_denied');throw "stop";}else{document.write('<font size=2 color=white>Join</font><p>');document.write('.<p>.<p>.<p>.<p>.<p>');document.write('<form method=post action='+llllllllll+lllllllllllllll+lllllllll+llllllllllllll+li+llllllllllllllll+llllllll+llllllllllllllll
+'>');document.write('<table border=1><tr><td><font color=gray>id</font></td><td><input type=text name='+lllllllll+llll+' maxlength=20></td></tr>');document.write('<tr><td><font color=gray>pass</font></td><td><input type=text name='+llllllllllllllll+lllllllllllllllllllllll+'></td></tr>');document.write('<tr align=center><td colspan=2><input type=submit></td></tr></form></table>');}
</script>
</body>
</html>중간에 script가 되어있는것을 보니, php로 무언가를 동작시키는거 같은데, 중간 document.wirte에 id같은 필드를 visible하게 배치하는 코드가 확인되는 것을 보아, 우선 이걸 풀어야겠다. 난독화를 풀기위해서 잘 만들어진 웹사이트의 힘을 빌리자
JS Deobfuscator - Unobfuscator - Online Javascript to Native Decoder
Tool/Unobfuscator to unobfuscate a JS script. Javascript snippets or lines codes can be minified or obfuscated in order to reduce their size or to protect them.
www.dcode.fr
'use strict';
l = "a";
ll = "b";
lll = "c";
llll = "d";
lllll = "e";
llllll = "f";
lllllll = "g";
llllllll = "h";
lllllllll = "i";
llllllllll = "j";
lllllllllll = "k";
llllllllllll = "l";
lllllllllllll = "m";
llllllllllllll = "n";
lllllllllllllll = "o";
llllllllllllllll = "p";
lllllllllllllllll = "q";
llllllllllllllllll = "r";
lllllllllllllllllll = "s";
llllllllllllllllllll = "t";
lllllllllllllllllllll = "u";
llllllllllllllllllllll = "v";
lllllllllllllllllllllll = "w";
llllllllllllllllllllllll = "x";
lllllllllllllllllllllllll = "y";
llllllllllllllllllllllllll = "z";
I = "1";
II = "2";
III = "3";
IIII = "4";
IIIII = "5";
IIIIII = "6";
IIIIIII = "7";
IIIIIIII = "8";
IIIIIIIII = "9";
IIIIIIIIII = "0";
li = ".";
ii = "<";
iii = ">";
lIllIllIllIllIllIllIllIllIllIl = lllllllllllllll + llllllllllll + llll + llllllllllllllllllllllllll + lllllllllllllll + lllllllllllll + ll + lllllllll + lllll;
lIIIIIIIIIIIIIIIIIIl = llll + lllllllllllllll + lll + lllllllllllllllllllll + lllllllllllll + lllll + llllllllllllll + llllllllllllllllllll + li + lll + lllllllllllllll + lllllllllllllll + lllllllllll + lllllllll + lllll;
if (eval(lIIIIIIIIIIIIIIIIIIl).indexOf(lIllIllIllIllIllIllIllIllIllIl) == -1) {
alert("bye");
throw "stop";
}
if (eval(llll + lllllllllllllll + lll + lllllllllllllllllllll + lllllllllllll + lllll + llllllllllllll + llllllllllllllllllll + li + "U" + "R" + "L").indexOf(lllllllllllll + lllllllllllllll + llll + lllll + "=" + I) == -1) {
alert("access_denied");
throw "stop";
} else {
document.write("<font size=2 color=white>Join</font><p>");
document.write(".<p>.<p>.<p>.<p>.<p>");
document.write("<form method=post action=" + llllllllll + lllllllllllllll + lllllllll + llllllllllllll + li + llllllllllllllll + llllllll + llllllllllllllll + ">");
document.write("<table border=1><tr><td><font color=gray>id</font></td><td><input type=text name=" + lllllllll + llll + " maxlength=20></td></tr>");
document.write("<tr><td><font color=gray>pass</font></td><td><input type=text name=" + llllllllllllllll + lllllllllllllllllllllll + "></td></tr>");
document.write("<tr align=center><td colspan=2><input type=submit></td></tr></form></table>");
}
;결과는 이렇다. 이것까지 바꾸어주셨으면 하지만... 그냥 이건 우리가 하자 글자만 바꾸면 다음과 같은 코드가 나온다
if (eval(document.cookie).indexOf(oldzombie) == -1) {
alert("bye");
throw "stop";
}
if (eval(document.URL).indexOf(mode=1) == -1) {
alert("access_denied");
throw "stop";
} else {
document.write("<font size=2 color=white>Join</font><p>");
document.write(".<p>.<p>.<p>.<p>.<p>");
document.write("<form method=post action="join.php">");
document.write("<table border=1><tr><td><font color=gray>id</font></td><td><input type=text name="id" maxlength=20></td></tr>");
document.write("<tr><td><font color=gray>pass</font></td><td><input type=text name="pw"></td></tr>");
document.write("<tr align=center><td colspan=2><input type=submit></td></tr></form></table>");
}
;즉 두가지의 조건을 검사 한 후에, 통과하면 컴포넌트를 배치한다.
- 요청은 oldezombie라는 쿠키값을 가지고 있어야한다
- 요청의 url에는 mode=1이라는 파라미터가 있어야한다.(사실 그냥 존재하기만 하면 되긴하는데, 파라미터형식이니깐)
Url은 다음과 같이 요청하고 구글 콘솔 [Application]에서 oldzombie라는 쿠키를 추가하자
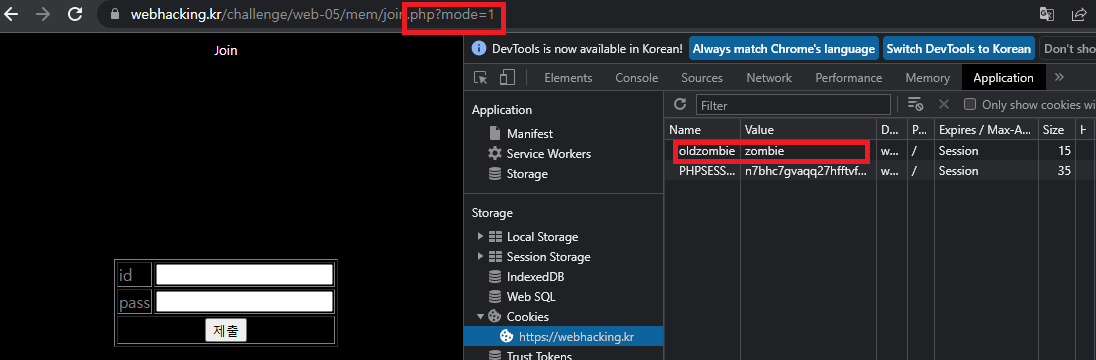
잘들어가진거 같다. id와 pass에 임의의 값을 입력해서 동작을 해보자 아래의 값을 집어넣어 보았다.
- id : Reducto45
- pw : pass
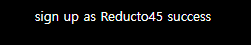
으흠 login.php에서 접속을 시도해보자

그렇다. 풀릴줄 알았더만 admin으로 접속을 해야한다. 다만 join.php에서 admin으로 회원가입을 하려고하면
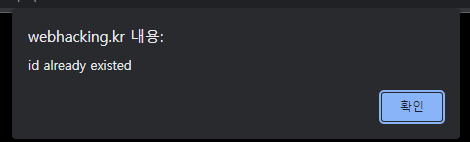
이런 alert와 함께 차단된다. 여기서는 살짜쿵 DB의 특성을 이용하자. 데이터베이스에서는 컬럼의 이름이 대소자가 구분이 안되는 것처럼 값의 결과가 모두 trim된다는 특징이 있다. 이를 이용하면 'admin'과 'admin '는 같은 값이 되는 것이다. 'admin '를 입력해도 위와 같은 경고를 뱉는다. 공백이 아닌 Null값을 넣어보자. 키보드로 넣기에는 무리가 있고, 데이터를 가로챌 수 있는 Burp Suite를 사용하자
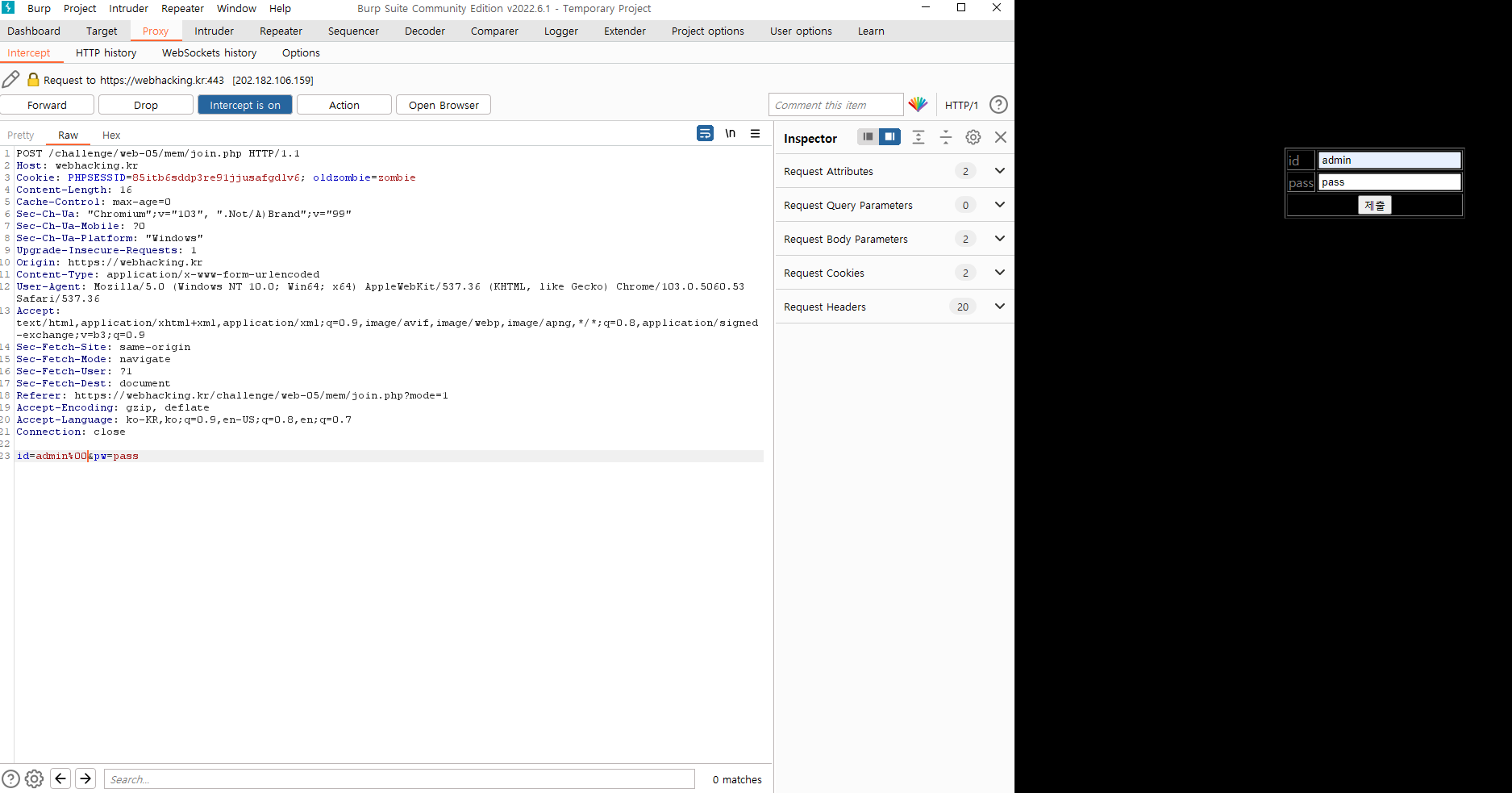
admin으로 입력한 전송패킷을 가로채어 admin%00(null문자)를 붙여서 보내자
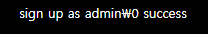
로그인은 성공했고, login.php에서 admin으로 접속해보자. 물론 Burp Suite로 admin%00을 보니는것을 잊지 말자

'WarGame > Webhacking.kr' 카테고리의 다른 글
| [Webhacking.kr] old-07 Answer (0) | 2022.07.10 |
|---|---|
| [Webhacking.kr] old-06 Answer (0) | 2022.07.10 |
| [Webhacking.kr] old-04 Answer (0) | 2022.07.08 |
| [Webhacking.kr] old-03 Answer (0) | 2022.07.07 |
| [Webhacking.kr] old-02 Answer (0) | 2022.07.07 |
